Your CRM is where conversations with customers live, invoices are tracked, and sensitive data is stored. In many ways, it’s the heart of your business operations, which makes protecting it a top priority.
The challenge is that not every CRM system offers the same level of security, and if something goes wrong, whether it’s a data breach or unauthorized access, the result isn’t just lost information, but lost customer trust. 🤝
This guide is here to help you understand CRM security. We’ll walk through what makes a CRM secure, the red flags to watch out for when you’re choosing a vendor, and a practical checklist you can use to keep your customer data safe.
At Method CRM, we’ve been supporting QuickBooks-based businesses since 2010. Small businesses choose us for our real-time two-way QuickBooks sync, customization services, and automation that keeps security front and center. By the end of this article, you’ll know how to spot a secure CRM and see how Method makes data protection part of every feature.🛡️
Table of Contents
- Multifactor or two-factor authentication
- Fine-grained permissions and access controls
- Encryption at rest and in transit
- Regular data backups and a disaster recovery plan
- Clear incident response procedures
- Compliance with GDPR/CCPA and a transparent privacy policy
- Evidence of active threat detection and monitoring
- Transparency about past security breaches
Why CRM security = trust 🔐
Customer trust isn’t built on features alone. It grows when you actively protect customer data and when customers come to learn this. A CRM holds sensitive data like payment records, contracts, and internal notes. Therefore, a single security breach could mean data loss, legal penalties, and a massive hit to customer trust.
Consider the stakes: Salesforce has experienced outages that left customer information inaccessible, while Microsoft Dynamics 365 has dealt with reported vulnerabilities that raised questions about incident response. These examples show that even industry leaders face security threats.
The bottom line is that when you invest in a CRM system, you’re both buying functionality and trusting that system to safeguard your entire business.
What makes a CRM secure? 🧐
When it comes to CRM security, there’s no single switch you can flip to guarantee safety. You’ll need to have the right layers in place to protect customer data at every step — from how people log in, to how information is stored, to how quickly a vendor responds if something goes wrong. Let’s look at the key pieces that make a CRM truly secure.
Authentication and access controls
Authentication is the first line of defence. Secure CRMs use multifactor authentication or two-factor authentication to verify user identity. But authentication alone isn’t enough.
Look for role-based permissions and access controls that let you assign the right level of access to each user. Following the “least privilege” principle helps prevent unauthorized access and keeps sensitive data locked down.
Weak passwords remain one of the biggest vulnerabilities. A secure CRM system should flag weak passwords and allow administrators to set requirements for stronger ones.
At Method CRM, authentication and permissions are baked in. Admins can fine-tune data access, ensuring only the right team members see the right customer data.
Data encryption and backups
A secure CRM must protect CRM data both at rest and in transit. That means strong data encryption when information is stored in the database and when it’s transmitted between devices.
Data backups are just as critical. Without them, a cyberattack or system failure can result in permanent data loss. Ask your CRM vendor how often they back up data, whether they offer point-in-time recovery, and how they test their backup integrity.
Method CRM includes regular data backups and secure storage practices to make sure sensitive customer data stays safe.
Threat detection and incident response
Cyber threats like phishing and malware are constantly evolving. That’s why a CRM system needs continuous threat detection to monitor for suspicious activity and send real-time alerts.
A transparent incident response plan is also essential. If potential breaches occur, you should know how quickly your CRM vendor will respond, how they’ll communicate with customers, and what steps they’ll take to contain the issue.
Method uses proactive monitoring, dashboards, and clear escalation protocols so customers aren’t left in the dark.
Compliance and certifications
Regulations like GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) require businesses to protect personal information and give customers more control over how their data is used.
When choosing a CRM vendor, ask about compliance and certifications such as SOC 2 or ISO 27001. These third-party audits confirm that a vendor has implemented robust security measures and strong security practices.
Red flags: When you can’t trust a CRM vendor 🚩
Not every CRM software provider takes security seriously. Watch out for these warning signs:
- No clarity on where your CRM data is stored.
- Limited or no security features are listed on their site.
- Dodging questions about cybersecurity or data access.
- Pushing automation without explaining the layer of security behind it.
- No clear plan for handling cyberattacks or data loss.
- Over-promising “seamless” integration without explaining how they protect against vulnerabilities.
If you see these signs, keep looking, as your customer trust is too valuable to risk.
The CRM security checklist ✅
Choosing a CRM is a big decision, and security should be at the top of your list. Here’s a detailed checklist to help you evaluate any CRM vendor.
Multifactor or two-factor authentication
Strong authentication prevents unauthorized access even if a password is stolen or guessed. Look for CRM systems that support multifactor authentication (MFA) or two-factor authentication (2FA), so users must confirm their identity with a code, app, or physical key.
Fine-grained permissions and access controls
Not everyone in your business needs to see everything. A secure CRM should let you set role-based permissions and granular access controls. That way, team members only access the customer data relevant to their role, reducing risks of internal misuse or accidental exposure.
Encryption at rest and in transit
Encryption is what keeps sensitive data unreadable to outsiders. Ask your CRM vendor whether data is encrypted both while stored on their servers (at rest) and while being transmitted between users and the system (in transit). If you want to protect financial records and customer information from cybercriminals, this is important.
Regular data backups and a disaster recovery plan
Hardware failures, human error, or cyberattacks can all cause data loss. A reliable CRM should perform automated, regular backups and have a disaster recovery plan in place. In turn, you’ll have the confidence that customer information can be restored quickly if something goes wrong.
Clear incident response procedures
No system is 100% immune to cyber threats. What matters is how a CRM vendor responds. Ask them about their incident response plan: how quickly do they alert customers, what steps do they take to contain potential breaches, and how do they prevent similar issues in the future?
Compliance with GDPR/CCPA and a transparent privacy policy
Data privacy regulations such as GDPR and CCPA hold businesses accountable for how they handle sensitive data. A trustworthy CRM vendor should comply with these standards and have a clear, easy-to-read privacy policy that explains how your customer data is stored, used, and shared.
Evidence of active threat detection and monitoring
A secure CRM shouldn’t just react to breaches but also detect potential threats before they escalate. Look for features like dashboards with suspicious activity logs, real-time monitoring, and automated alerts. These show that the vendor takes proactive steps to guard against cyberattacks and phishing attempts.
Transparency about past security breaches
No vendor is perfect, but honesty goes a long way. If a CRM vendor has faced security breaches before, find out how they handled the situation, what changes they made afterward, and how they’ll keep your data safe going forward.
Use this checklist to evaluate if a CRM system is secure and trustworthy enough for your business.
🔐 Authentication & Access Controls
- Supports multi-factor authentication (MFA)
- Enables role-based permissions for different users
- Offers granular access controls (field or record level)
- Can lock or deactivate users instantly
🧱 Data Protection
- Data encrypted at rest and in transit
- Regular data backups and restoration available
- Offers data masking or pseudonymization
- Clear on data storage location
🛡️ Threat Detection & Incident Response
- Provides activity monitoring and logs
- Includes a documented incident response plan
- Notifies you of potential breaches
- Ability to audit user and permission changes
📜 Privacy & Compliance
- Compliant with GDPR, CCPA, or similar regulations
- Supports custom data retention policies
- Handles data access requests (DSARs)
- Transparent about data sharing & third-party access
🚩 Red Flags to Watch For
- No clear security documentation
- Avoids questions about breach history
- Doesn’t let you manage permissions or backups
- Uses vague buzzwords instead of clear functionality
- Unclear on data residency and protection
Why Method is a secure CRM you can trust 🙌
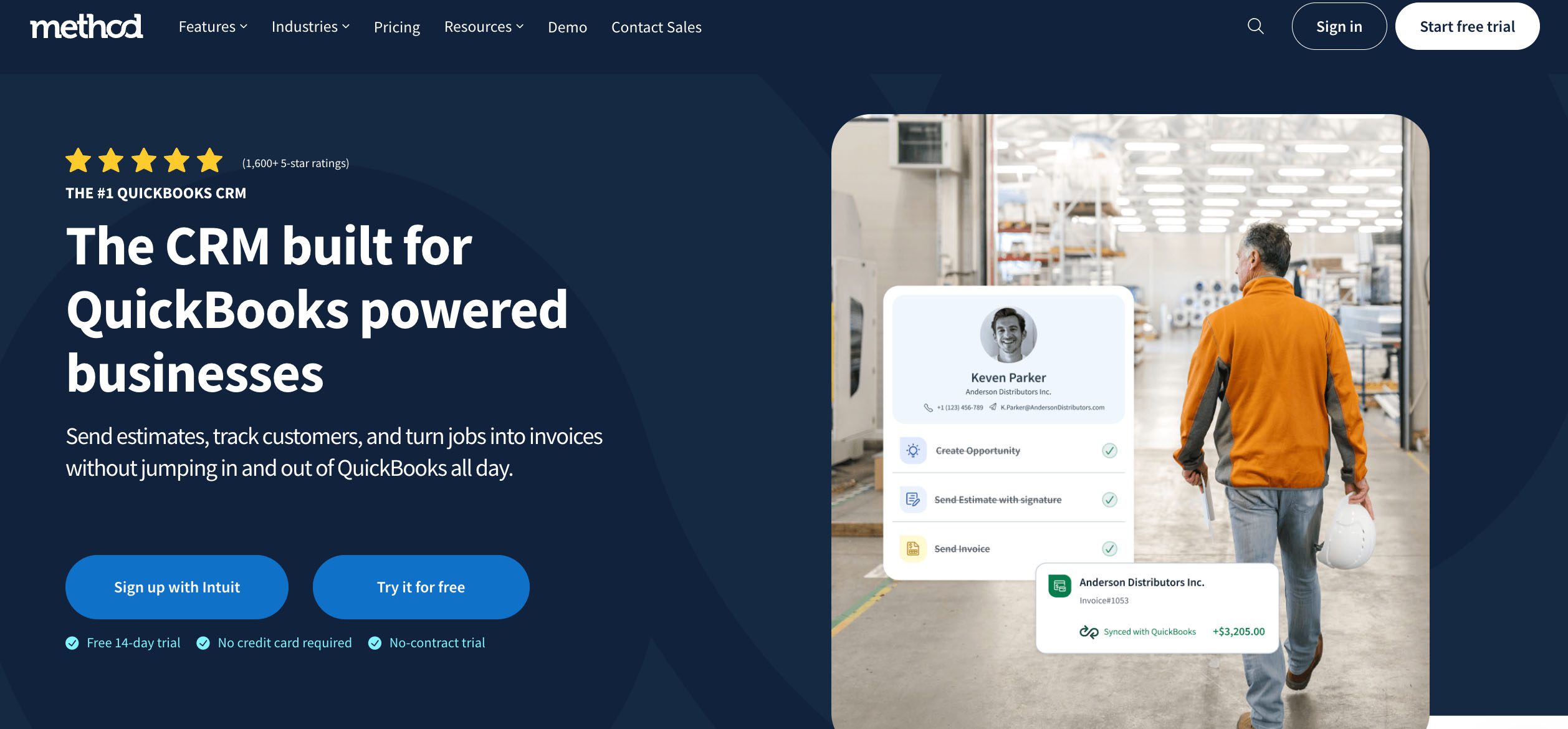
Method CRM is built for small businesses that want the power of automation without compromising on CRM security. With real-time QuickBooks sync, strong authentication options, flexible permissions, and transparent incident response protocols, Method makes security part of your everyday workflow.
Method offers robust security measures in a streamlined package. Our customers know exactly how their data is handled, with full control over data access and visibility into our security features.
That’s why many small businesses trust Method as their secure CRM system. It’s powerful, flexible, and built with customer trust at its core.
Closing thoughts 💬
A CRM isn’t valuable unless it keeps your data safe. First and foremost, it needs to protect sensitive information about your customers, your business, and your financials.
Use the checklist, ask vendors the tough questions, and don’t settle for vague promises. At Method, we’re committed to being transparent and reliable so you can focus on building strong customer relationships.
Ready to see our secure CRM system in action? Book a demo of Method today.






